Network Security Overview
In this guide, we present a list of the possible attack types that can occur in communication between two parties, as well as the two possible network security models.
Types of Attacks
- We can divide possible attacks into two types:
Passive Attacks
- Listen attack (information disclosure):
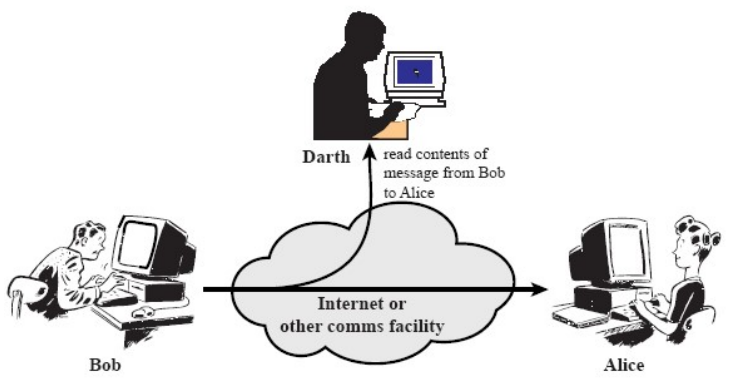
Fig.1: Example of an information disclosure listen attack
- Listen attack (traffic analysis):
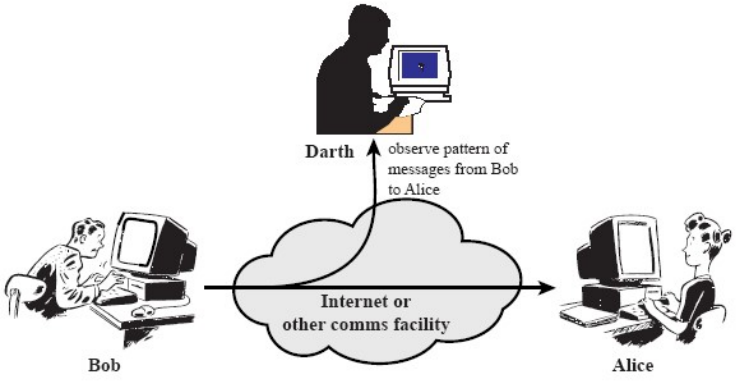
Fig.2: Example of a traffic analysis listen attack
Active attacks
- Tampering attack:
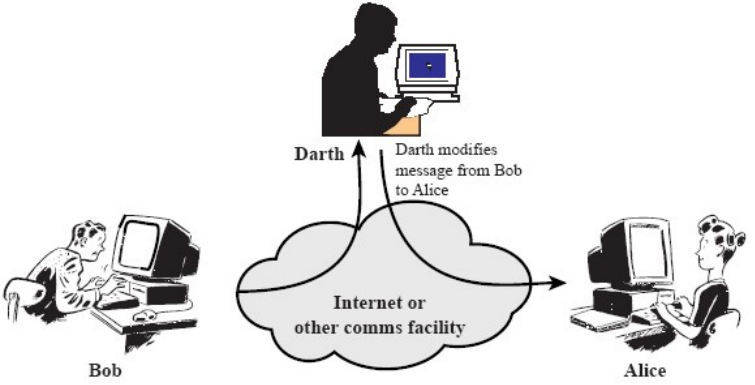
Fig.3: Example of a tampering attack
- Impersonation attack:
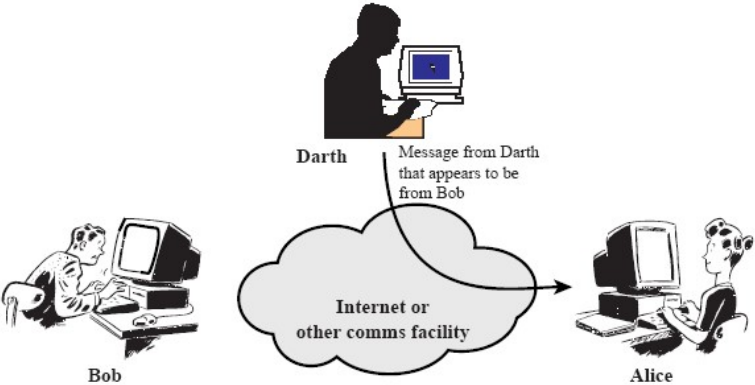
Fig.4: Example of an impersonation attack
- Replay attacks:
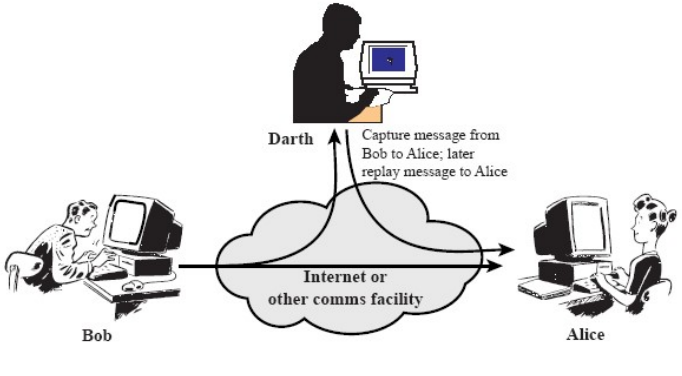
Fig.5: Example of a replay attack
- DDOS (denial of service attacks):
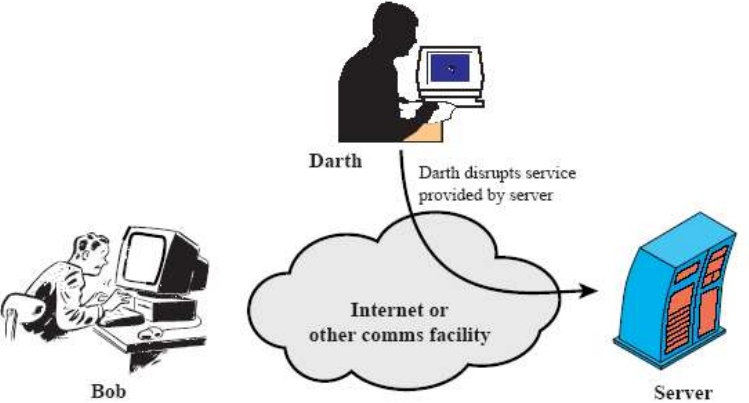
Fig.6: Example of a denial of service attack (Bob and other legitimate users cannot access the web server)
Network Security Models
- There are two network security models:
1. Gateway
- E.g.: Firewall
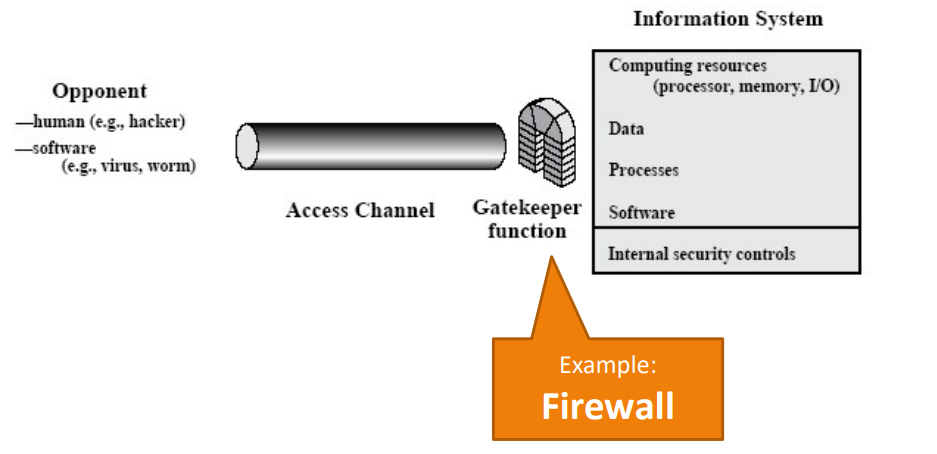
Fig.7: Example of a security model using a firewall
2. Secure Channel
- E.g.: TLS/SSL
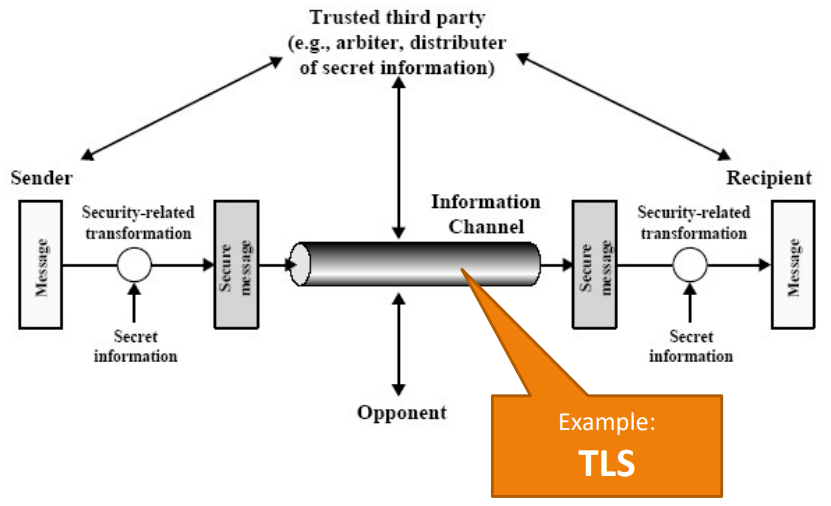
Fig.8: Diagram of how a secure channel works